I think it is the best option of all the possible choices I have seen and I can see how the 'Open' they tacked on is required for finding the project through searches. Adoption would have been be awful if they stuck with just 'Tofu'. Adoption of tofu as a meat substitute could have improve, though.
The Terrawork (Terragrunt) people have posted their latest response. It looks like multiple companies have banded together and are fully behind forking Terraform, if required.
https://blog.gruntwork.io/the-future-of-terraform-must-be-open-ab0b9ba65bca
Yup, that is for the AWS CLI command. You could also use that from AWS Cloud Shell.
You can use aws iam list-instance-profiles to get a list of what is already created. I suspect there is something else wrong.
It cloud be looking for the default Beanstalk instance profile and role (aws-elasticbeanstalk-ec2-role) as it isn't auto-created anymore. It could also be a permission issue with the role's policy.
https://docs.aws.amazon.com/elasticbeanstalk/latest/dg/iam-instanceprofile.html
Elastic Beanstalk is one of the few AWS services I haven't used as it just deploys a number of other services and resources behind the scenes. It is more of a up-and-running-quick demonstration tool than something you would use IRL. It can be used, but there are better options.
An instance profile is what I would call a legacy resource that really shouldn't be needed, but is still there in the background for backwards compatibility. You can't attach an IAM role directly to an EC2 instance. You need to have an instance profile in between that is named the same as the IAM role.
You can create one using every other interface (command line, CloudFormation, Terraform, SDKs, etc.), but not through the web console (browser). From the web console, you would need to recreate the IAM role and make sure you select EC2 as the purpose/service for the role. Only then will it create a matching instance profile along-side your new IAM role.
I picked up a Hakko desoldering gun many years ago to save me from this. It was pricey (~$300), but has been worth it over the years.
It is preferable to have the dock power the laptops. Then there is only 1 cable to plug in. If your personal laptop has a USB-C power, it can probably be powered through it. Plugging it in to you work laptop power supply shouldn't break it as there is a lot of negotiating taking place before power is provided. You may want to search the internets first.
The Dell docks are also universal and will work. Avoid HP as they are proprietary. Some other brands (Plugable, Anker) work really well, but may not include the power adapter. Make sure you include the power adapter when comparing docks. I would get the new 100W USB-C adapters (UGreen or Anker) that can power your dock, devices, and laptop (by way of the dock).
I use a mix of Dell and Anker USB-C docks with Dell, HP, and Macbooks and run up to dual 4K displays and power the laptops (The HPs are limited).
There is a few things to watch out for. You laptop's USB-C port needs to be a Thunderbolt port to work with a Thunderbolt dock. If it isn't, you will need non-Thunderbolt USB-C dock.
The port needs to support Power Delivery (PD) and may still limit charging to 60W. You should get up to 82W after the dock takes its cut. Some laptops (Dell) support higher charging rates only with their own brand docks. If you are gaming, your battery will drain, just slowly.
The port should support Displayport even if you are using HDMI. Most docks will have a mix of DP and HDMI. You will need an ACTIVE DP to HDMI adapter. If one of your monitors has DP, use that insteaad of an adapter.
Are we the lobsters?
We have a slack channel where we dump a number of cloud/service outage RSS feeds into. Github has always dominated that channel.
Aligning the Alfines involves putting them into 4th gear and turning the fine adjustment on the shift until the yellow lines on the hub line up. It can easily be done every time you plan to use the bike. It is just easy to forget to do.
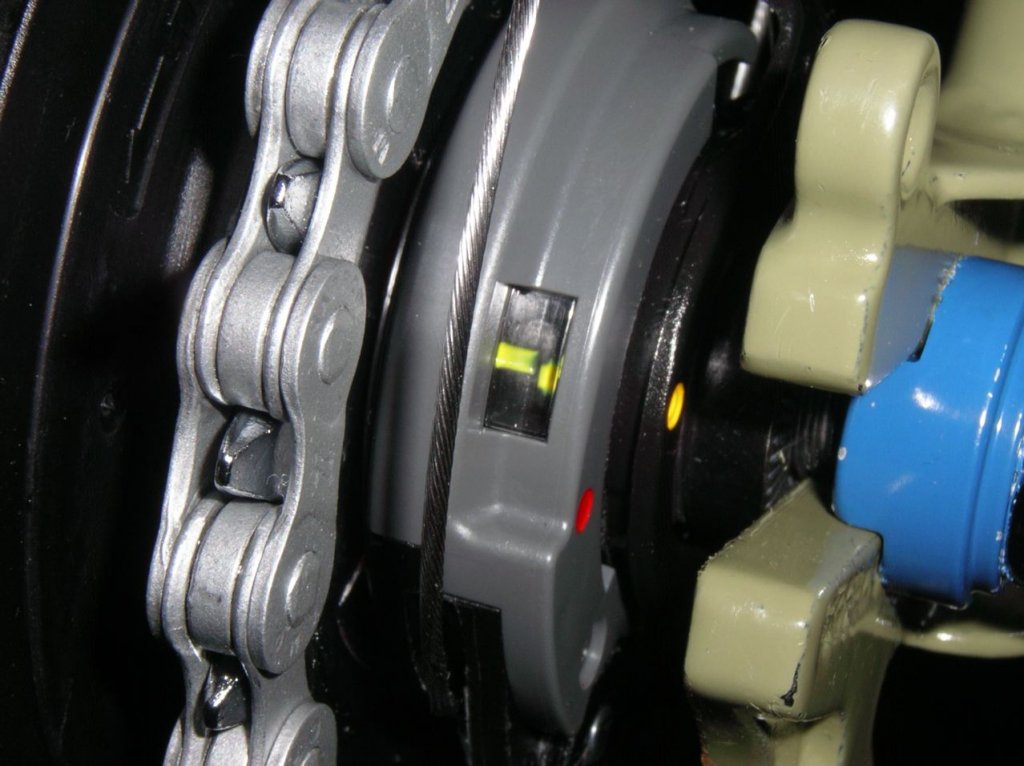
As for dealing with wheel re-installation and shifter cable reattachment , I customized a spanner to perfectly fit between the hub and the dropouts to either hold the hub in place while tightening the axle nuts or loading tension when installing the when reconnecting the shifter cable. I can't remember which. It might have been both.

After having failure issues using an Alfine 11 with a 29+ MTB (high torque setup), I have used nothing but cassette based drivetrains on everything but my folding bike. Also, my only local hub re-builder has stopped providing that service and Universal Cycles stopped carrying replacement internals, so I will probably not use an Alfine IGH on any new bikes.
I have an Alfine 11 and 8 still mount in wheelsets for my folding bike and I think I have another Alfine 11 in parts. The Alfine 8 is bomb proof; the 11 much less so. If you religiously keep them in alignment they will last. If you ride on them while misaligned, you will wear down the pawls and start loosing gears. After that you need to do a rebuild and very few places do that.
Also, avoid using them in 29"wheels. It is too much torque for them, and the pawls will wear down within a year or two.
They are stupid fast for up shifting as you can do it under some load and the shifting is instant. The other nice perk is that you can downshift while stopped. No need to lift the back wheel and let it spin.
Winter commuting is where they shine. I have to replace my whole drivetrain every winter on my cassette bikes. The IGHs are completely unaffected by the abuse. The grease/oil lubricant used inside does start to thicken up and add some resistance starting out, but that only happens below about -7c.
If you need the gear range of the Alfine 11 I would suggest considering a Rohloff speedhub instead, but they are 3 times the price.
I got approved a few months ago and will have solar panels installed in the next few months. I am happy to hear there will be a second stage as I want to get my windows replaced next. If AB could elect a competent government I would also replace my mid-efficient furnace.